On your slack channel, add the 'email integration' app. Once done, Slack will provide you an email address with slack.com domain. Emails sent to this address will be imported into your slack channel. Then, on SNS create an email subscription and provide the slack email above. Amazon Web Services Inc. SNS topic notifications to developers’ Slack channels or Chime chat rooms. Administrators can add the alerts to Slack from directly within the AWS Chatbot. Aws-sns-slack-terraform is a Terraform module. You just need to include the module in one of your Terraform scripts and set up SNS topics and permissions. See examples/ for concrete examples.
By default, when managing a large number of EC2 instances, you don't get a lot of visibility into how your instances are behaving. Any monitoring beyond what you get in the console needs to be configured and set up by the AWS user using services like Cloudwatch or Cloudtrail, etc.
EC2 instances can be started or stopped for various reasons by anyone with access to the EC2 console, and your team might want to know about it.
In Zuar's case we manage hundreds of EC2 instances across three regions running our products Mitto, Rapid Portal and Custom Portal. We wanted to get notifications in our #devops slack channel anytime an instance state changed.
If you're familiar with Terraform feel free to skip everything below! Simply Edit and use this code.
Overview
AWS Cloudwatch allows you to create rules which will publish to an SNS topic any time a specific EC2 instance or list of instances has a state change. You can subscribe emails to this SNS topic and receive emails anytime there's a new SNS publication. In this case, we'll subscribe a custom Lambda function, that formats the slack message, and then makes a POST request to our slack channel.
Flow
- A user on your AWS account stops an EC2 instance.
- Your Cloudwatch Event Rule is triggered and publishes to your SNS Topic
- SNS invokes your Lambda function with the message Cloudwatch published
- Your Lambda function formats the message for slack and does a POST request to your webhook.
Aws Cloudwatch Sns Slack
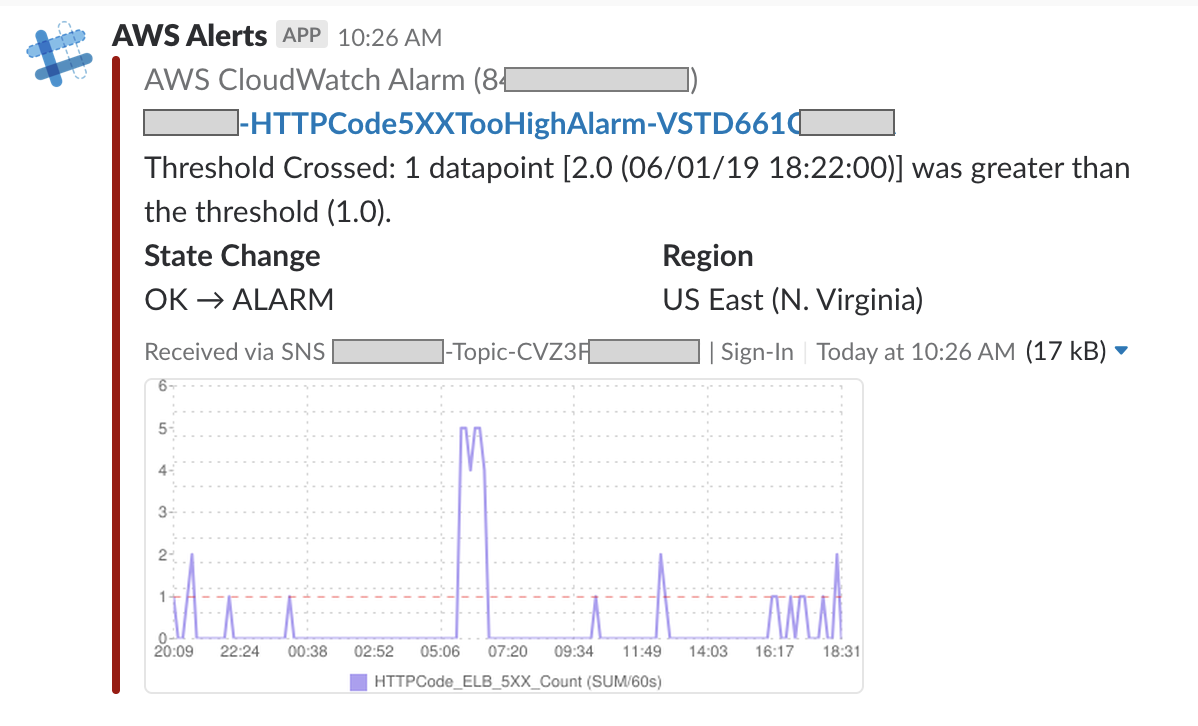
Results
The messages in your slack channel should look something like this:
Slack Webhook
Aws Sns Slack Interview
First and foremost, you need a Slack channel with an incoming webhook. It should give you a link similar to this which we will use later in our Lambda function: https://hooks.slack.com/services/UNIQUE_ID/UNIQUE_ID/UNIQUE_ID .. You can test that the link is working using curl like this:
Lambda Function

I won't get into the specifics of Lambda deployment here. It'll need an execution role, a policy, and a policy attachment, some of which the console will create for you. Later you will add a trigger for SNS. Our Lambda uses Python3.6 and there are 4 environment variables you will need to set. ACCESSKEY, SECRETKEY, REGION and SLACK_HOOK. Below is our lambda function:
NOTE: When packaging this for deployment, be sure to include requests as a dependency.
Simple Notification Service (SNS)
Still with me? Next you'll need to create an SNS topic, and then create a subscription with your Lambda function. In the SNS console you would click 'Create Topic'. All you need here is a name. Once that's done, you'll go to 'Subscriptions' and create a subscription. enter the ARN for the topic you just created, select 'AWS Lambda' as the protocol, and then select the ARN for the Lambda we created.
Cloudwatch Rule
In the Cloudwatch console. Click on 'Rules' under events in the menu on the left. Click on 'Create Rule'. On the left select 'Event Pattern', service 'EC2', event type 'EC2 Instance State-change Notification'. Select 'Any state' and 'Any Instance' to publish to SNS on changes to any instance in this region.
On the right select 'SNS Topic' at the top then select the SNS topic you created. Below that select 'input transformer'. In the first textarea use:
and in the Second textarea use:
Aws Sns Slack Login
Our Lambda function will expect the format above.
Aws Sns Slack Software
Save your changes, and it's time to do some testing.
Testing and Troubleshooting
Aws Sns Slack 連携
To test everything we just created, simply go to the EC2 console and start and stop an instance you're not using in the region you created your resources in. If you don't get a message in your slack channel, check the cloudwatch logs for your Lambda function and ensure that the function was invoked. If the function was not invoked, you might need an SNS trigger on your Lambda function. Also double check you have all the permissions, roles, and policies you need for Lambda to receive events and be invoked by SNS.
